Android Malware Analysis Series - ATO.apk - Part 3.1

File Information:
ATO Australian Taxation Office
Sample Source:
SHA256 Hash:
Initial APK Signature 55884b3b0018b42e500c8ca427d8ae3b3174d9efca5aa57b34eb9202cb84913a
Introduction
This Android malware sample surfaced through a Twitter account Malware Hunter Team. It appears to be impersonating the Australian Taxation Office. Not quite sure what the delivery method to the victim is but it turned out to be fun sample with some anti-detection techniques built in by the malware author. I split this blog post up into two sections. Section 4.1 details the initial analysis of the first APK and its underlying contents. Such as the AndroidManifest.xml file, permissions, components, and examining file contents.
Part 3.2 will examining the packaged .so files with ghidra, the secondary stage apk payload with jadx-gui, and the anti-debugging / emulation present in the Android malware code.
Decompilation and Analysis
As per my prior posts in the series I typically like to decompile the apk with apktool and do some preliminary analysis with jadx-gui to get an idea of what the Android malware is doing once installed on the victims device.
AndroidManifest.xml file
Permissions
Here is a verbose list of the permissions described in the AndroidManifest.xml file. I will not go into to detail as to what each permission does I will leave that exercise up to the reader. But will call them out as needed in the sections below.
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.REQUEST_INSTALL_PACKAGES"/>
<uses-permission android:name="android.permission.USE_FINGERPRINT"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.READ_CALL_LOG"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NOTIFICATION_POLICY"/>
<uses-permission android:name="android.permission.WRITE_SETTINGS"/>
<uses-permission android:name="com.moutai.mall.permission.PUSH_PROVIDER"/>
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED"/>
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<uses-permission android:name="com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<uses-permission android:name="android.permission.QUICKBOOT_POWERON"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" android:maxSdkVersion="29"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE" android:maxSdkVersion="29"/>
<uses-permission android:name="com.moutai.mall.permission.PROCESS_PUSH_MSG"/>
<uses-permission android:name="android.permission.RECEIVE_LAUNCH_BROADCASTS"/>
<uses-permission android:name="android.permission.DISABLE_KEYGUARD"/>
<uses-permission android:name="android.permission.GET_TASKS"/>
<uses-permission android:name="android.permission.LOCK_DEVICE"/>
<uses-permission android:name="android.permission.BLUETOOTH"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
<uses-permission android:name="android.permission.ACTION_MANAGE_OVERLAY_PERMISSION"/>
<uses-permission android:name="android.permission.SYSTEM_ALERT_WINDOW"/>
[TRUNCATED]
<uses-permission android:name="android.permission.ACCESS_CONTENT_PROVIDERS_EXTERNALLY"/>
<uses-permission android:name="android.permission.CALL_PHONE"/>
<uses-permission android:name="android.permission.SEND_SMS"/>
<uses-permission android:name="android.permission.ACTION_MANAGE_OVERLAY_PERMISSION"/>
<uses-permission android:name="com.google.android.gms.permission.ACTIVITY_RECOGNITION"/>
<uses-permission android:name="com.huawei.appmarket.service.commondata.permission.GET_COMMON_DATA"/>
<uses-permission android:name="android.permission.QUERY_ALL_PACKAGES"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-permission android:name="android.permission.MODIFY_AUDIO_SETTINGS"/>
<uses-permission android:name="android.permission.WAKE_LOCK"/>
<uses-permission android:name="android.permission.GET_PACKAGE_SIZE"/>
<uses-permission android:name="android.permission.WRITE_CONTACTS"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.ACCESS_BACKGROUND_LOCATION"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="com.meizu.flyme.permission.PUSH"/>
<uses-permission android:name="android.permission.WRITE_SECURE_SETTINGS"/>
<uses-permission android:name="android.permission.MANAGE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.MANAGE_APP_OPS_MODES"/>
<permission android:name="com.moutai.mall.permission.PROCESS_PUSH_MSG" android:protectionLevel="signatureOrSystem"/>
<permission android:name="com.moutai.mall.permission.PUSH_PROVIDER" android:protectionLevel="signatureOrSystem"/>
<permission android:name="com.moutai.mall.permission.PUSH_WRITE_PROVIDER" android:protectionLevel="signatureOrSystem"/>
<uses-permission android:name="android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS"/>
<uses-permission android:name="android.permission.MODIFY_PHONE_STATE"/>
<uses-permission android:name="android.permission.WRITE_CALL_LOG"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE"/>
Activities
Each of the components present in the AndroidManifest.xml file point to obfuscated attribute names and when attempting to locate the the fully qualified class name that it points to in the package tree of jadx-gui we see that it is missing. This is a pretty common method that Android malware authors use to try and hide malicious behavior. Either loading the classes from an apk, dex, or jar file obfuscated in the package directory on the device.
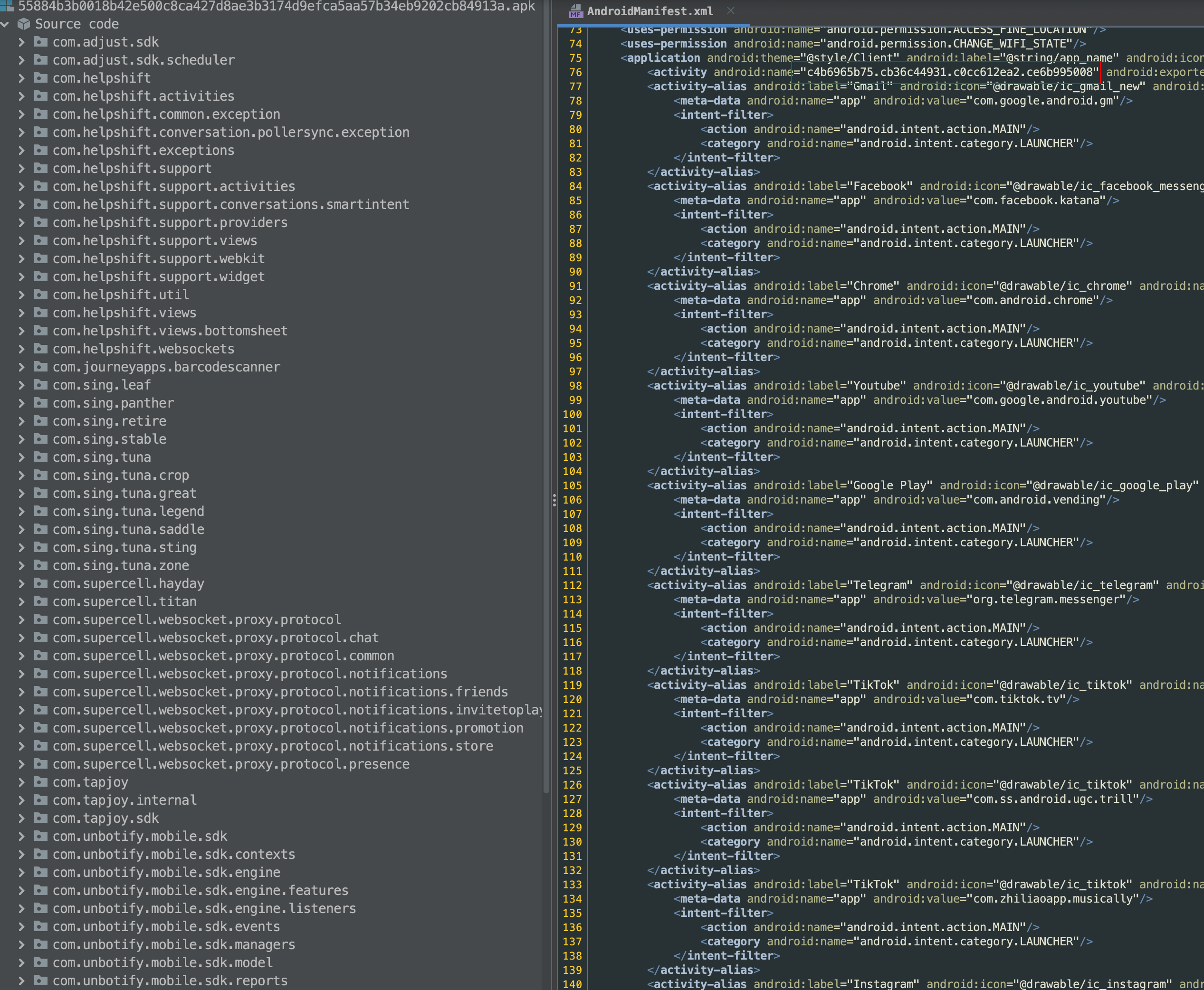
Example of missing classes in the Jadx-gui package tree view on the left
As an example the activity below uses multiple attribute aliases in the activity that appear to be associated with other installed applications. Digging further into the attribute tags for the meta-data sub-elements name and value they appear to be point to identifiers linked with the name and possibly the package directory.
<activity android:name="c4b6965b75.cb36c44931.c0cc612ea2.ce6b995008" android:exported="true"/>
<activity-alias android:label="Gmail" android:icon="@drawable/ic_gmail_new" android:name="c4b6965b75.cb36c44931.GmailNew" android:enabled="false" android:targetActivity="c4b6965b75.cb36c44931.c0cc612ea2.ce6b995008" android:noHistory="true" android:roundIcon="@drawable/ic_gmail_new">
<meta-data android:name="app" android:value="com.google.android.gm"/>
<intent-filter>
<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>
</intent-filter>
[TRUNCATED]
<activity-alias android:label="Bank of America Mobile Banking" android:icon="@drawable/ic_bank_of_america" android:name="c4b6965b75.cb36c44931.BOFA" android:enabled="false" android:targetActivity="c4b6965b75.cb36c44931.c0cc612ea2.ce6b995008" android:noHistory="true" android:roundIcon="@drawable/ic_bank_of_america">
<meta-data android:name="app" android:value="com.infonow.bofa"/>
<intent-filter>
<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>
</intent-filter>
[TRUNCATED]
Based on the brief snippet of the attribute and elements we can see one that points to Bank of America Mobile Banking. If we search the package name via Google it appears to point to the following value attribute com.infonow.bofa. See highlighted URL below.
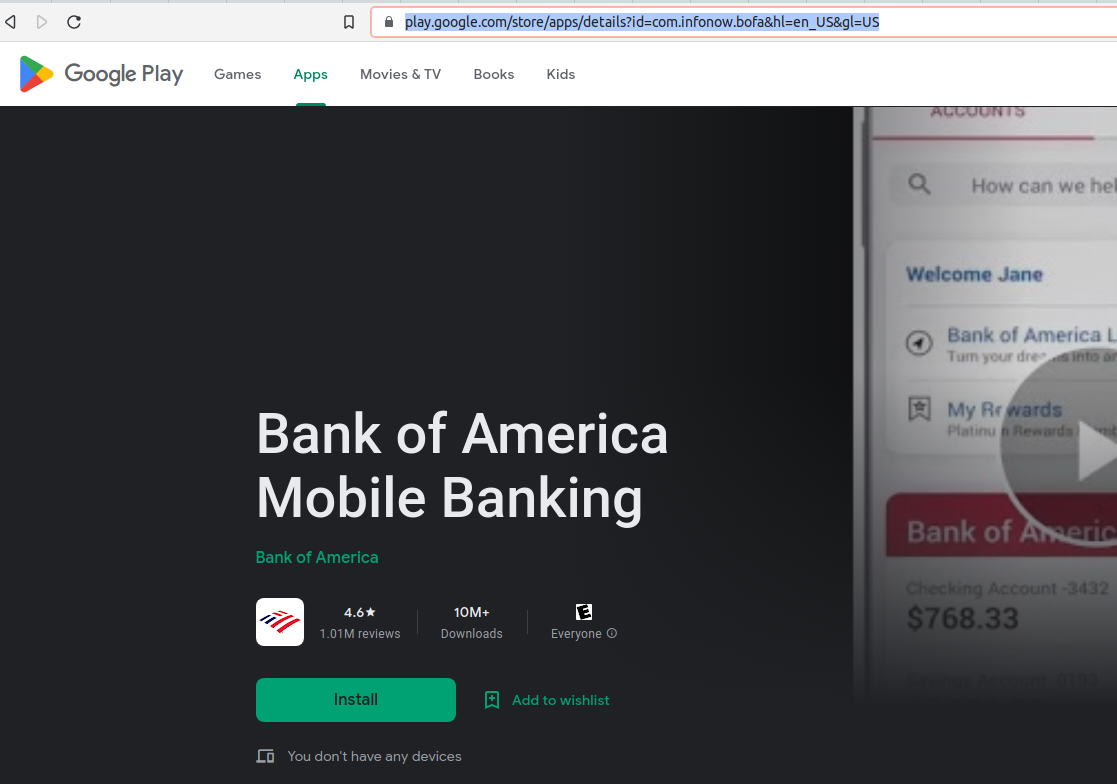
Example screenshot of BOA package name
SMS Components
The below chunk of code from the AndroidManifest.xml file corresponds to SMS communication on the device. Lets break down each component further in this code block pulled from the xml file. Which I will later breakdown in part two and assess the secondary APK file that corresponds to the obfuscated class names.
The following activity ca0f9b0f97 appears to be related to sending a message. We can see in the Android documentation here. That the constant value matches the ACTION_SENDTO. Which indicates that this activity is related to sending sms mms via the applications activity.
<activity android:name="c4b6965b75.cb36c44931.c409757303.c0cc612ea2.ca0f9b0f97">
<intent-filter>
<action android:name="android.intent.action.SEND"/>
<action android:name="android.intent.action.SENDTO"/>
<data android:scheme="sms"/>
<data android:scheme="smsto"/>
<data android:scheme="mms"/>
<data android:scheme="mmsto"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
</intent-filter>
</activity>
The service cedf9842b9 below appears to be related to sms and mms messages sent from the caller or device. If we look at the TelephonyManager section here we can observe the corresponding URI schema to describe how a message is sent to a recipient with the message and number using the data elements described in the intent filter.
<service android:name="c4b6965b75.cb36c44931.c409757303.c2860135ed.cedf9842b9" android:permission="android.permission.SEND_RESPOND_VIA_MESSAGE" android:exported="true">
<intent-filter>
<action android:name="android.intent.action.RESPOND_VIA_MESSAGE"/>
<category android:name="android.intent.category.DEFAULT"/>
<data android:scheme="sms"/>
<data android:scheme="smsto"/>
<data android:scheme="mms"/>
<data android:scheme="mmsto"/>
</intent-filter>
</service>
The following receiver c2b996a875 uses the SMS_DELIVER constant value which is related to the SMS_DELIVER_ACTION. If you are interested read more here in the Android documentation. As pointed out in the documentation this component requires the permission RECEIVE_SMS which is called out in the AndroidManidest.xml file earlier. My hunch is that this receiver will deal with stealing received messages from the users device.
<receiver android:name="c4b6965b75.cb36c44931.c409757303.c34b13876d.c2b996a875" android:permission="android.permission.BROADCAST_SMS">
<intent-filter>
<action android:name="android.provider.Telephony.SMS_DELIVER"/>
</intent-filter>
</receiver>
The following receiver ce88792f9c pertains to new WAP PUSH messages that have been received by the device. Typically this intent will only be delivered to the default SMS application on the device. If you would like to read more and overview the needed permissions follow this link.
<receiver android:name="c4b6965b75.cb36c44931.c409757303.c34b13876d.ce88792f9c" android:permission="android.permission.BROADCAST_WAP_PUSH" android:enabled="true">
<intent-filter>
<action android:name="android.provider.Telephony.WAP_PUSH_DELIVER"/>
<data android:mimeType="application/vnd.wap.mms-message"/>
</intent-filter>
</receiver>
Admin Receiver
This receiver c04f5ddb69 deals with various admin related permissions. Searching the Android documentation we see the description for DeviceAdminReceiver this receiver appears to be asking for system level admin permissions on the device. Currently we cannot see the class methods and their underlying functions, but this gives us a good nudge as to the class purpose in the application. Since all three of the action elements and name attributes are intended to manage the device as a device administrator.
<receiver android:name="c4b6965b75.cb36c44931.c34b13876d.c04f5ddb69" android:permission="android.permission.BIND_DEVICE_ADMIN" android:exported="true">
<intent-filter>
<action android:name="android.app.action.DEVICE_ADMIN_ENABLED"/>
<action android:name="android.app.action.DEVICE_ADMIN_DISABLED"/>
<action android:name="android.app.action.DEVICE_ADMIN_DISABLE_REQUESTED"/>
</intent-filter>
<meta-data android:name="android.app.device_admin" android:resource="@xml/admin"/>
The exported receiver c158375cfb sets multiple elements and attributes related to what appear to be admin level device actions. A quick overview of the core functionality shows that the receiver can turn the screen on and off, perform various boot operations, and possibly examine the external applications available.
<receiver android:name="c4b6965b75.cb36c44931.c34b13876d.c158375cfb" android:enabled="true" android:exported="true">
<intent-filter>
<action android:name="android.intent.action.BOOT_COMPLETED"/>
<action android:name="android.intent.action.LOCKED_BOOT_COMPLETED"/>
<action android:name="android.intent.action.ACTION_POWER_CONNECTED"/>
<action android:name="android.intent.action.BATTERY_OKAY"/>
<action android:name="android.net.wifi.WIFI_STATE_CHANGED"/>
<action android:name="android.intent.action.SCREEN_OFF"/>
<action android:name="android.intent.action.DREAMING_STOPPED"/>
<category android:name="android.intent.category.HOME"/>
<category android:name="android.intent.action.QUICKBOOT_POWERON"/>
<action android:name="android.net.conn.CONNECTIVITY_CHANGE"/>
<action android:name="android.intent.action.ACTION_POWER_DISCONNECTED"/>
<action android:name="android.intent.action.BATTERY_LOW"/>
<action android:name="android.intent.action.SCREEN_ON"/>
<action android:name="android.intent.action.BATTERY_CHANGED"/>
<action android:name="android.intent.action.REBOOT"/>
<action android:name="android.intent.action.EXTERNAL_APPLICATIONS_AVAILABLE"/>
<action android:name="com.htc.intent.action.QUICKBOOT_POWERON"/>
</intent-filter>
</receiver>
Respawn Receiver
The following code snippet for the receiver ce1771ebca appears to be associated with respawning the application. Either for upgrade or evasion purposes. I will analyze this in part two to verify its intended use.
<receiver android:name="c4b6965b75.cb36c44931.c34b13876d.ce1771ebca" android:enabled="true" android:exported="true">
<intent-filter>
<action android:name="respawnService"/>
</intent-filter>
</receiver>
Data Exfiltration Activity
The activity GIgAlTeTdGtDzZaDtHnTeKuDpFgXgHmSdRa is a possible indicator of data exfiltration from the device. Using the attributes VIEW and BROWSE for each data element mime type that could be tied to installed applications or telephony activities such as calls, texts, and voice messages.
<activity android:name="c4b6965b75.cb36c44931.GIgAlTeTdGtDzZaDtHnTeKuDpFgXgHmSdRa" android:exported="true" android:launchMode="singleTask" android:configChanges="smallestScreenSize|screenSize|uiMode|screenLayout|orientation|navigation|keyboardHidden|keyboard|locale" android:resizeableActivity="true">
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:mimeType="audio/*"/>
<data android:mimeType="application/ogg"/>
<data android:mimeType="video/mp4"/>
<data android:mimeType="video/mpeg4"/>
<data android:mimeType="video/3gpp"/>
<data android:mimeType="video/webm"/>
<data android:mimeType="application/mp4*"/>
<data android:mimeType="application/mpeg*"/>
<data android:mimeType="application/xspf+xml"/>
<data android:mimeType="application/x-mpegurl"/>
</intent-filter>
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:mimeType="audio/*" android:scheme="http"/>
<data android:mimeType="application/ogg" android:scheme="http"/>
<data android:mimeType="video/mp4" android:scheme="http"/>
<data android:mimeType="video/mpeg4" android:scheme="http"/>
<data android:mimeType="video/3gpp" android:scheme="http"/>
<data android:mimeType="application/mp4*" android:scheme="http"/>
<data android:mimeType="application/mpeg*" android:scheme="http"/>
<data android:mimeType="application/xspf+xml" android:scheme="http"/>
<data android:mimeType="application/x-mpegurl" android:scheme="http"/>
<data android:mimeType="audio/*" android:scheme="https"/>
<data android:mimeType="application/ogg" android:scheme="https"/>
<data android:mimeType="video/mp4" android:scheme="https"/>
<data android:mimeType="video/mpeg4" android:scheme="https"/>
<data android:mimeType="video/3gpp" android:scheme="https"/>
<data android:mimeType="application/mp4*" android:scheme="https"/>
<data android:mimeType="application/mpeg*" android:scheme="https"/>
<data android:mimeType="application/xspf+xml" android:scheme="https"/>
<data android:mimeType="application/x-mpegurl" android:scheme="https"/>
</intent-filter>
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<data android:mimeType="audio/*" android:scheme="rtsp"/>
<data android:mimeType="application/ogg" android:scheme="rtsp"/>
<data android:mimeType="video/mp4" android:scheme="rtsp"/>
<data android:mimeType="video/3gpp" android:scheme="rtsp"/>
</intent-filter>
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<data android:mimeType="*/*" android:scheme="file" android:host="*" android:pathPattern=".*\\.webm"/>
<data android:mimeType="*/*" android:scheme="content" android:host="*" android:pathPattern=".*\\.webm"/>
</intent-filter>
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:mimeType="audio/x-mpegurl" android:scheme="http"/>
<data android:mimeType="audio/mpegurl" android:scheme="http"/>
<data android:mimeType="application/vnd.apple.mpegurl" android:scheme="http"/>
<data android:mimeType="application/x-mpegurl" android:scheme="http"/>
</intent-filter>
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:host="*" android:pathPattern=".*\\.m3u"/>
<data android:host="*" android:pathPattern=".*\\.m3u8"/>
<data android:host="*" android:pathPattern=".*\\.mp3"/>
<data android:host="*" android:pathPattern=".*\\.3gp"/>
<data android:host="*" android:pathPattern=".*\\.mp4"/>
</intent-filter>
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:scheme="http" android:host="*" android:pathPattern=".*\\.m3u"/>
<data android:scheme="http" android:host="*" android:pathPattern=".*\\.m3u8"/>
<data android:scheme="http" android:host="*" android:pathPattern=".*\\.mp3"/>
<data android:scheme="http" android:host="*" android:pathPattern=".*\\.3gp"/>
<data android:scheme="http" android:host="*" android:pathPattern=".*\\.mp4"/>
<data android:scheme="https" android:host="*" android:pathPattern=".*\\.m3u"/>
<data android:scheme="https" android:host="*" android:pathPattern=".*\\.m3u8"/>
<data android:scheme="https" android:host="*" android:pathPattern=".*\\.mp3"/>
<data android:scheme="https" android:host="*" android:pathPattern=".*\\.3gp"/>
<data android:scheme="https" android:host="*" android:pathPattern=".*\\.mp4"/>
<data android:scheme="rtsp" android:host="*" android:pathPattern=".*\\.m3u"/>
<data android:scheme="rtsp" android:host="*" android:pathPattern=".*\\.m3u8"/>
<data android:scheme="rtsp" android:host="*" android:pathPattern=".*\\.mp3"/>
<data android:scheme="rtsp" android:host="*" android:pathPattern=".*\\.3gp"/>
<data android:scheme="rtsp" android:host="*" android:pathPattern=".*\\.mp4"/>
<data android:scheme="rtmp" android:host="*" android:pathPattern=".*\\.m3u"/>
<data android:scheme="rtmp" android:host="*" android:pathPattern=".*\\.m3u8"/>
<data android:scheme="rtmp" android:host="*" android:pathPattern=".*\\.mp3"/>
<data android:scheme="rtmp" android:host="*" android:pathPattern=".*\\.3gp"/>
<data android:scheme="rtmp" android:host="*" android:pathPattern=".*\\.mp4"/>
<data android:scheme="mms" android:host="*" android:pathPattern=".*\\.m3u"/>
<data android:scheme="mms" android:host="*" android:pathPattern=".*\\.m3u8"/>
<data android:scheme="mms" android:host="*" android:pathPattern=".*\\.mp3"/>
<data android:scheme="mms" android:host="*" android:pathPattern=".*\\.3gp"/>
<data android:scheme="mms" android:host="*" android:pathPattern=".*\\.mp4"/>
</intent-filter>
</activity>
Apktool Decompilation
Assets folder
After initial decompilation with apktool and analysis we can see various xml files and two lib directories packaged into this APK.
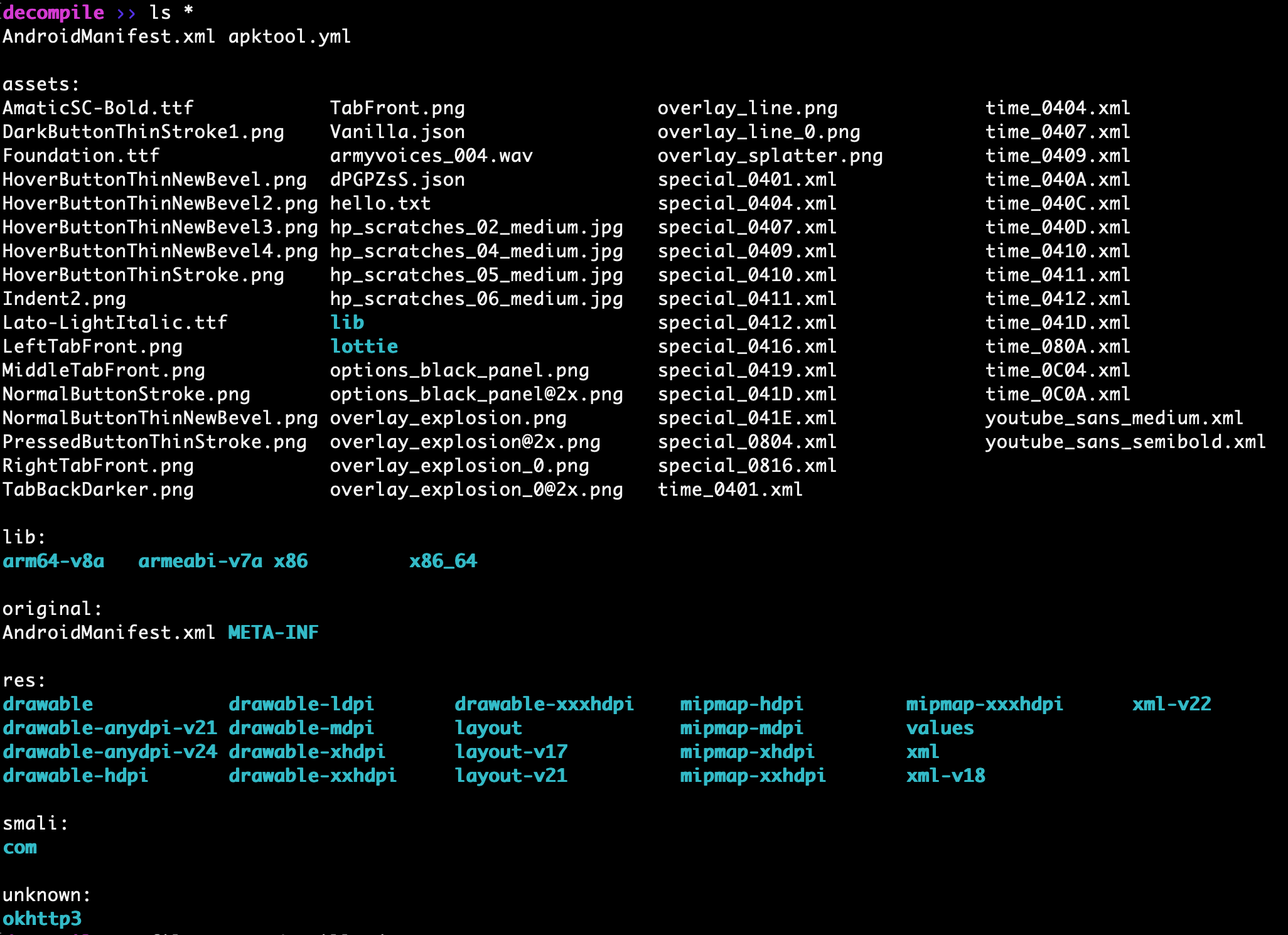
Example of quick file check after decompilation
For performing various manual tests against the files in the decompiled APK I like to use grep, file and some quick bash scripts to check the validity of the file types and naming convention. This is helpful in enumerating common files used by malware authors to hide APKs, dex, or jar files that can be loaded as a secondary stage payloads to perform malicious activity on the device.
A quick over view of the xml files under the assets directory. Which all appear to be standard xml based files.
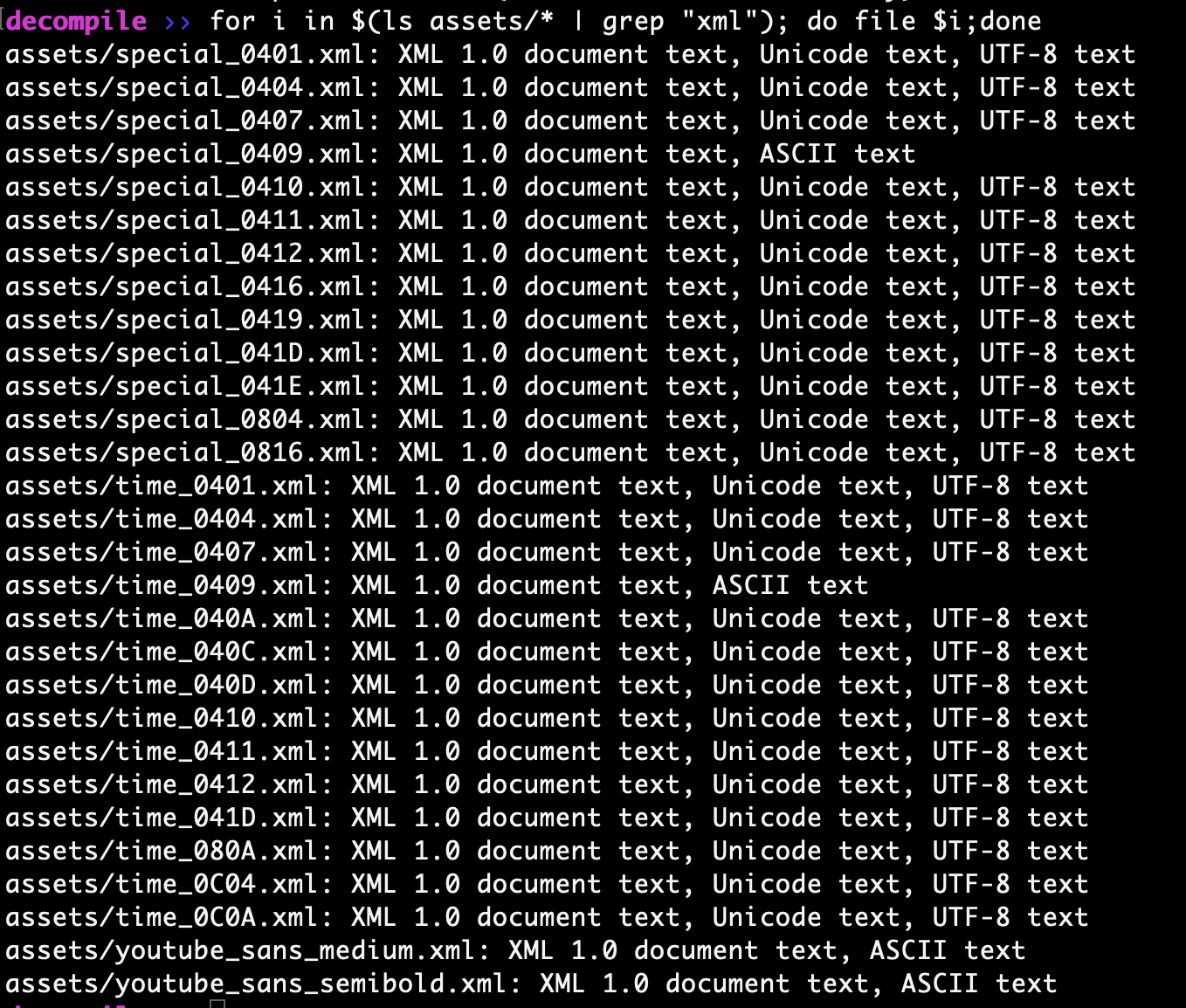
Checking XML file integrity under assets directory
A few additional XML files were found with non-standard titles. Such as ic_paypal.xml, ic_citibak.xml, and ic_bank_of_america.xml just to name a few. Which may point to the malware examining other applications that could be installed on the device and exfiltrating data to be pushed to a command and control server at a later point.
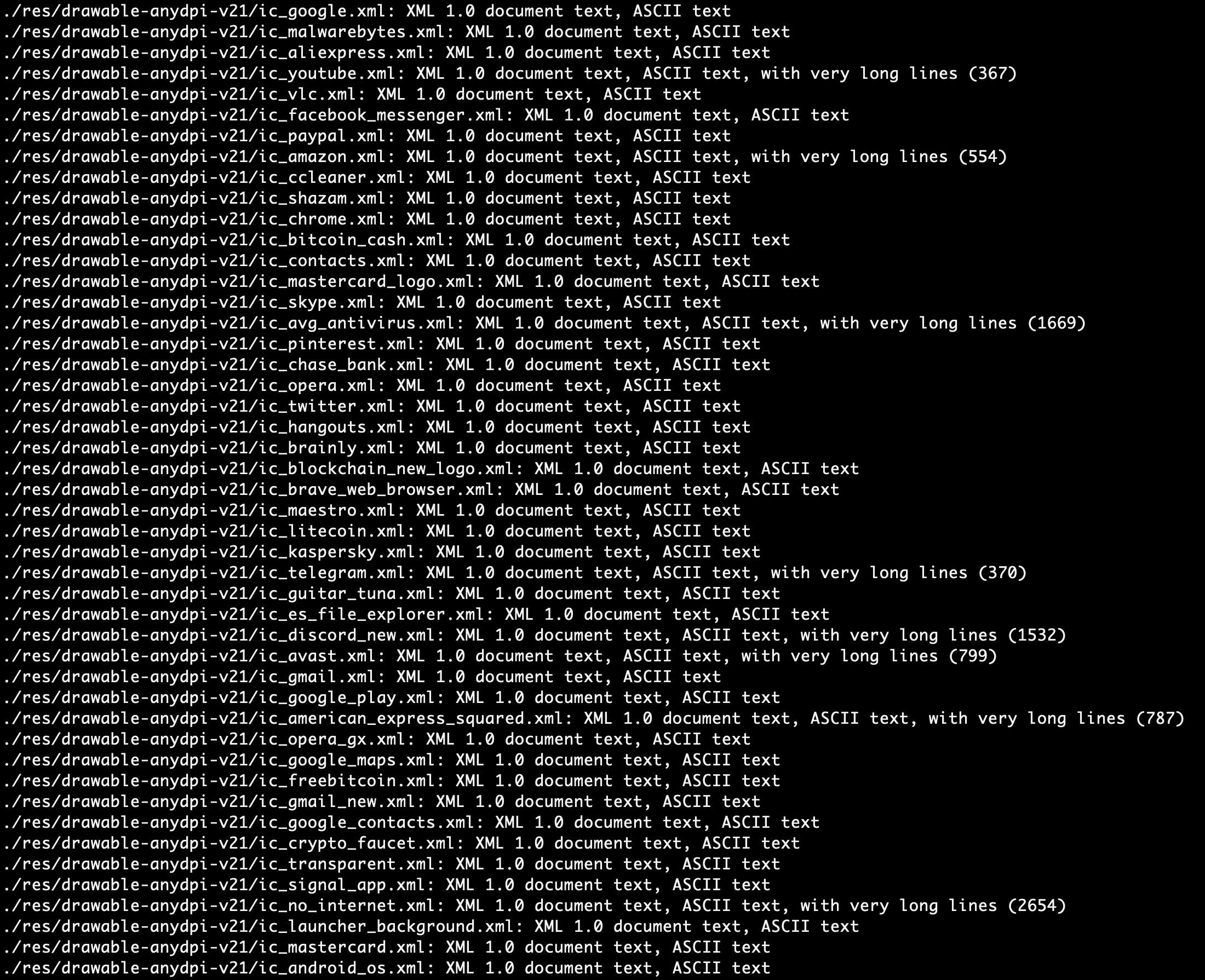
Strange XML files group 1
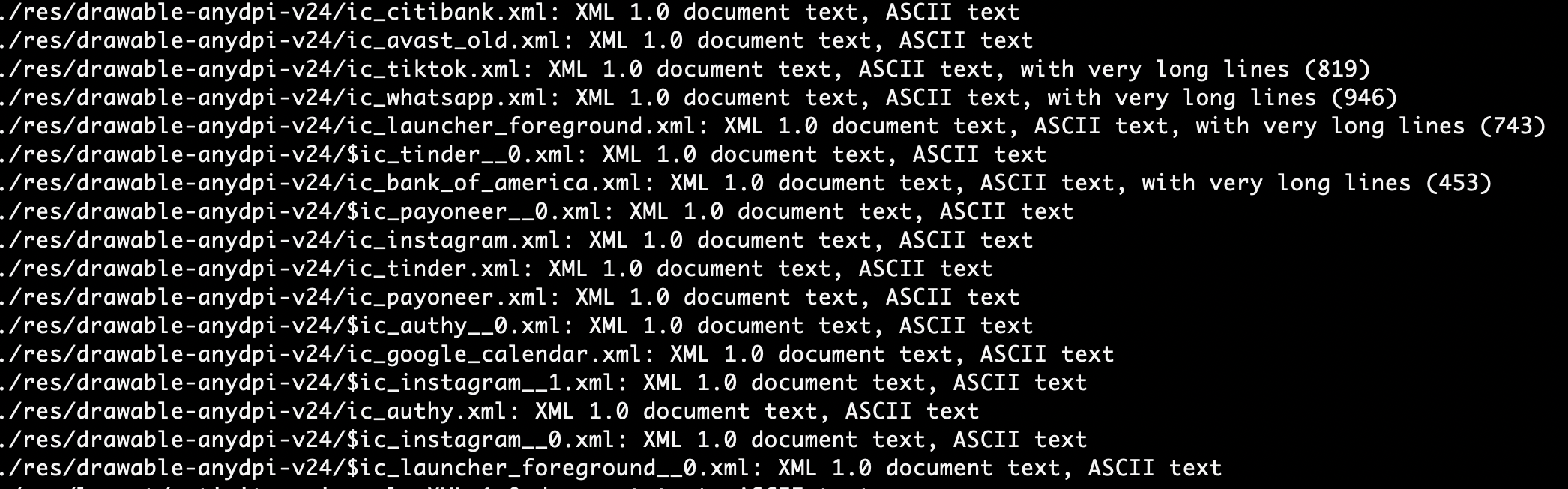
Strange XML files group 2
Two lib directories were present in the decompiled application. Commonly applications use the default lib directory under the applications root directory to load native code into the applications context. This could be another indicator of Android malware using non-standard locations for loading binaries at runtime. Below are the two lib directories with binary file names such as libEncryptorP.so and libterminal.so
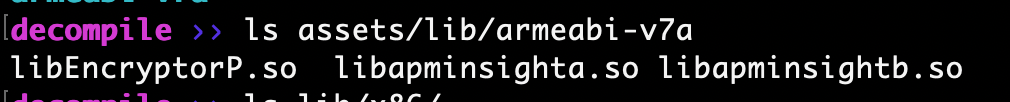
Lib folder under assets directory
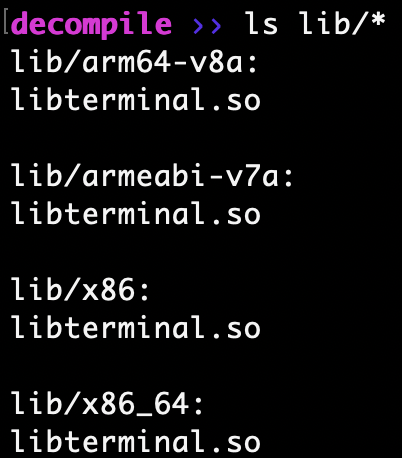
Standard lib directory for all arch types
The following JSON files were present in the decompiled APK. Though each JSON file appeared to be correctly identified with the file type except for the dPGPZsS.json file. This file will be further analyzed during the installation and part two portion of this blog post.
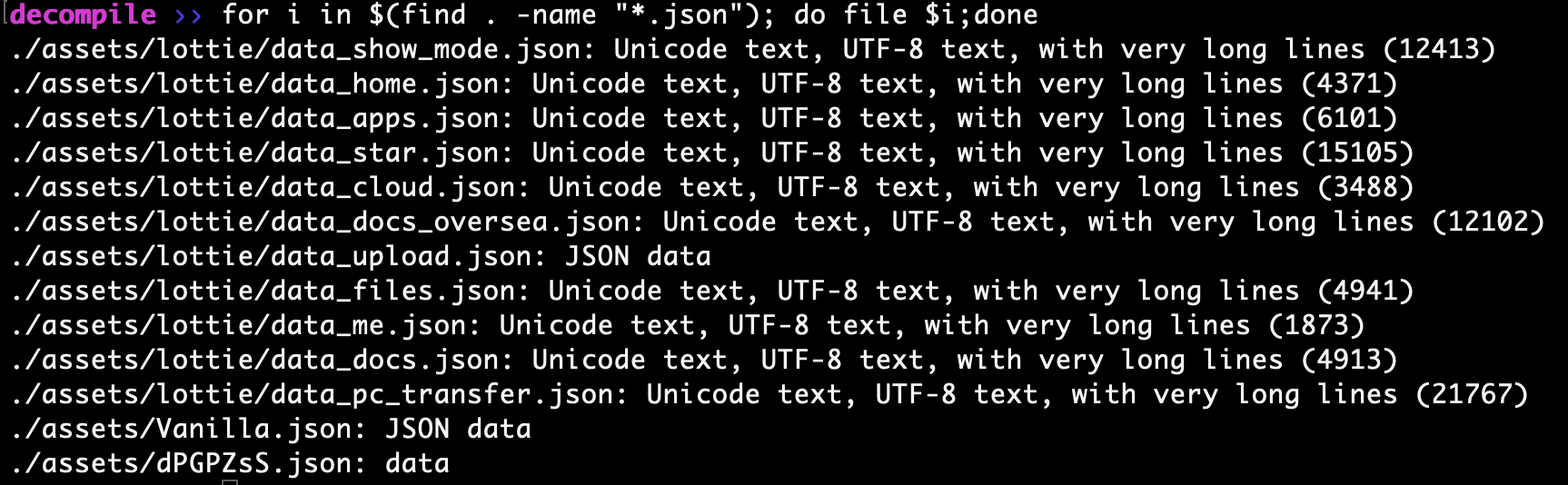
Example output of JSON files under decompiled apk folder
I did one last test case against the APKs file structure. I attempted to locate any zip files that may be present. Only one was present which appeared to be part of the okhttp3 library implemented in the application.

For loop to search for zip files
Dynamic Analysis
Installation
Using adb I installed the APK onto an emulated Android Studio device. Below is a screenshot of the application icon.
Screenshot of ATO application icon
After attempting to open the application on the device there is no foreground view or foreground activity present. There may be an initial detection present on start up for either an emulated device, debugging, or root.
Frida shows the package name and associated PID though it is running in the background we do not have a foreground activity.
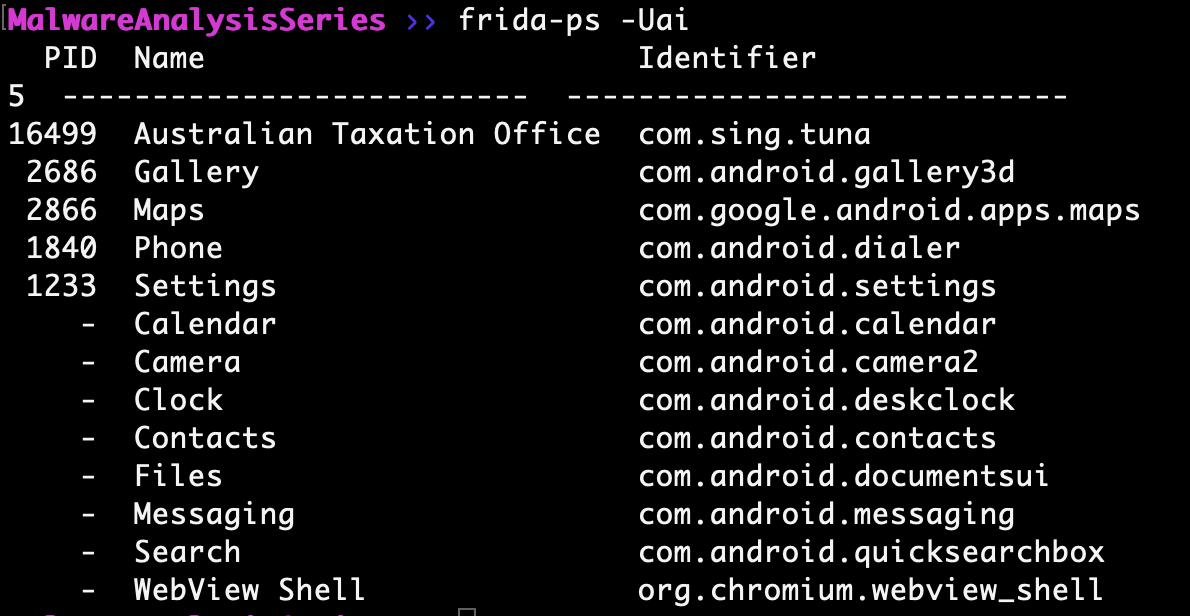
Examine application process with frida
Attempting to attach frida to the running process it is immediately terminated. This may be an sign of anti-debugging implemented by the malware authors. So as to deter reverse engineering of the application at runtime.
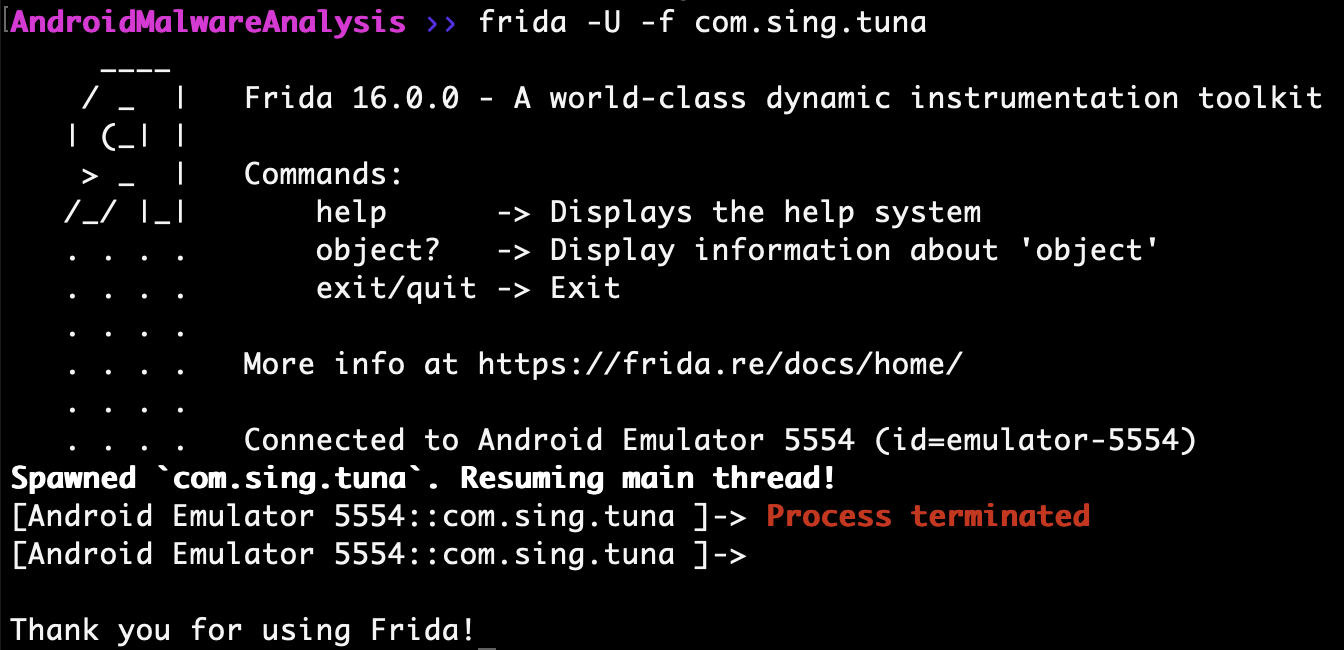
Frida terminated
This section will further elaborated in part two of this blog post. I will detail possible work arounds and steps to bypass the detection mentioned above.
Post Installation File Analysis
After initial analysis of the application at start up or the failure to start a foreground activity and debug the application I pivoted to examining the applications files under the default /data/data directory.
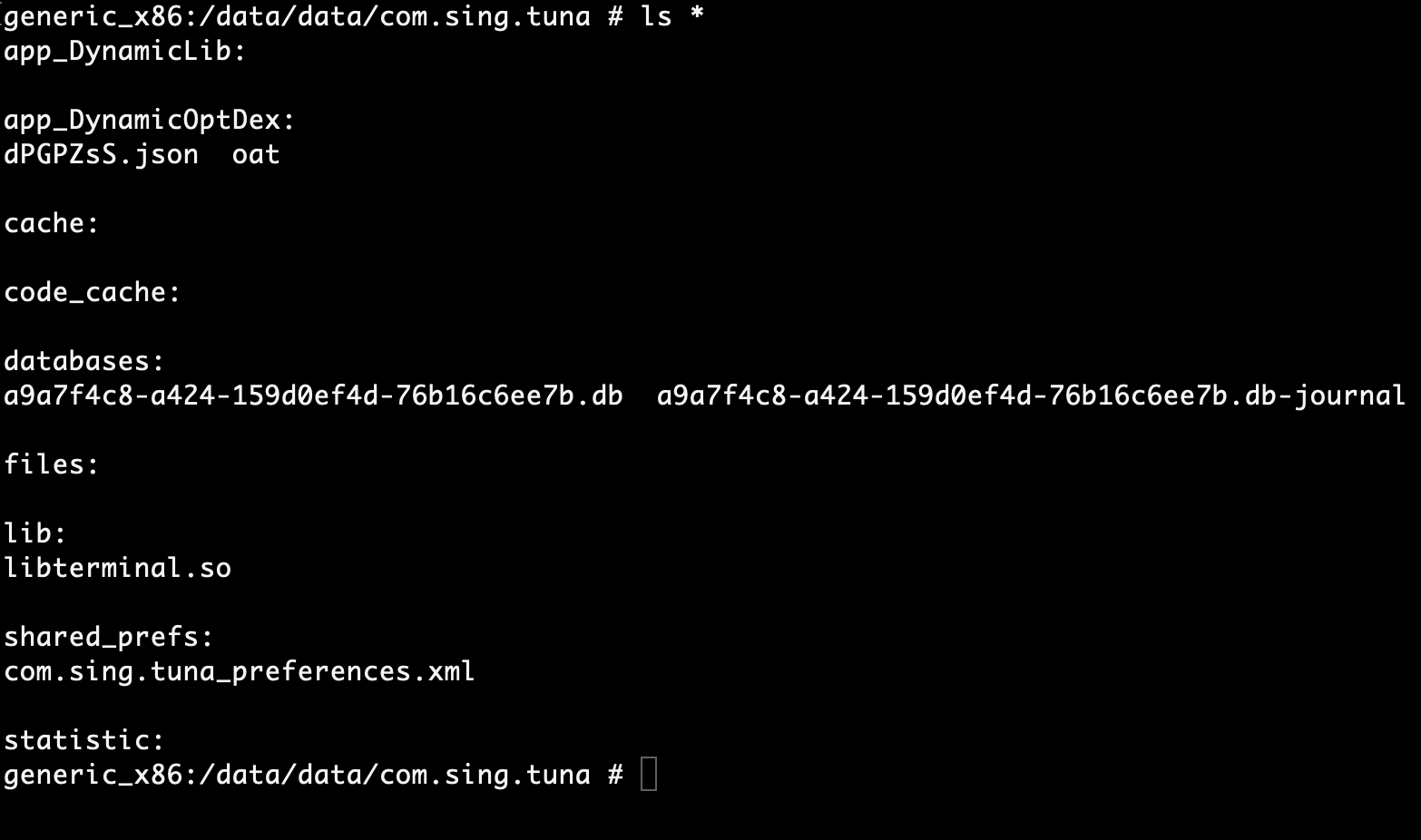
Example output of application directory
Hidden APK
We can see the dPGPZsS.json file mentioned in the decompiled APK before is present. Interestingly the folder associated with loading the file appears to be subtitled with dynamic dex. This is a possible indicator of a dynamically loaded APK, jar or dex file.
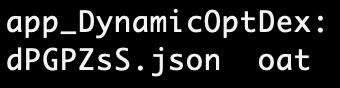
Folder contents
Running file against json file shows that it is a zip archive indicating a APK file. To potentially load other classes referenced in the initial APK.
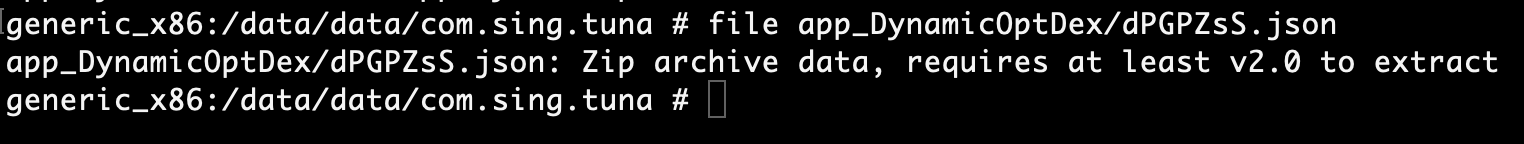
File type output
A secondary file was also present. Which we may need to investigate further.
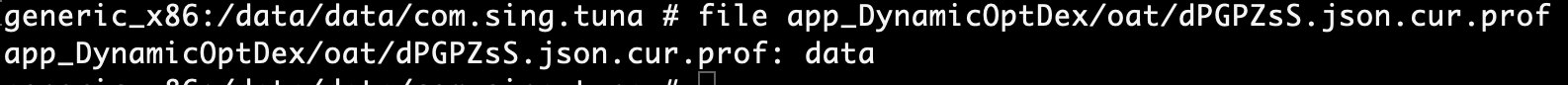
Lib Directory
After initial investigation and analysis of the lib directory. It appears there is a binary file that has a suspicious looking name similar to what we found in the decompilation section. Extra time will be taken to analyze it in ghidra or r2 this will be done in part two of this blog post.
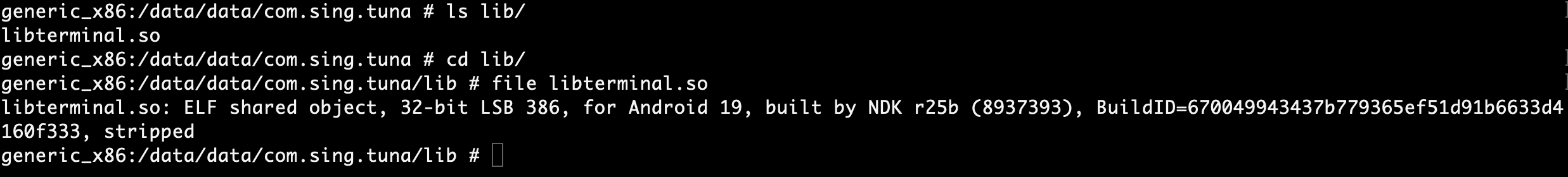
lib file verification
Fishy XML File
The following xml file appeared as part of the initial installation on the emulated device. It seems to reference a set of encoded xml strings used by the application.
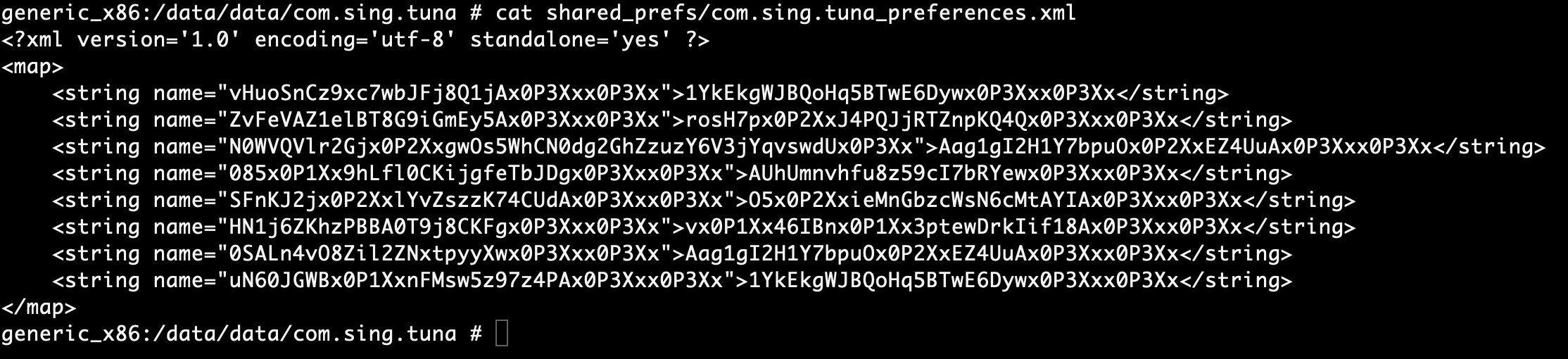
Encoded strings
Conclusion
This concludes part one of this post. In the second part I will be examining the four .so files with ghidra, the secondary stage apk payload with jadx-gui, and the anti-debugging / emulation present in the Android code.